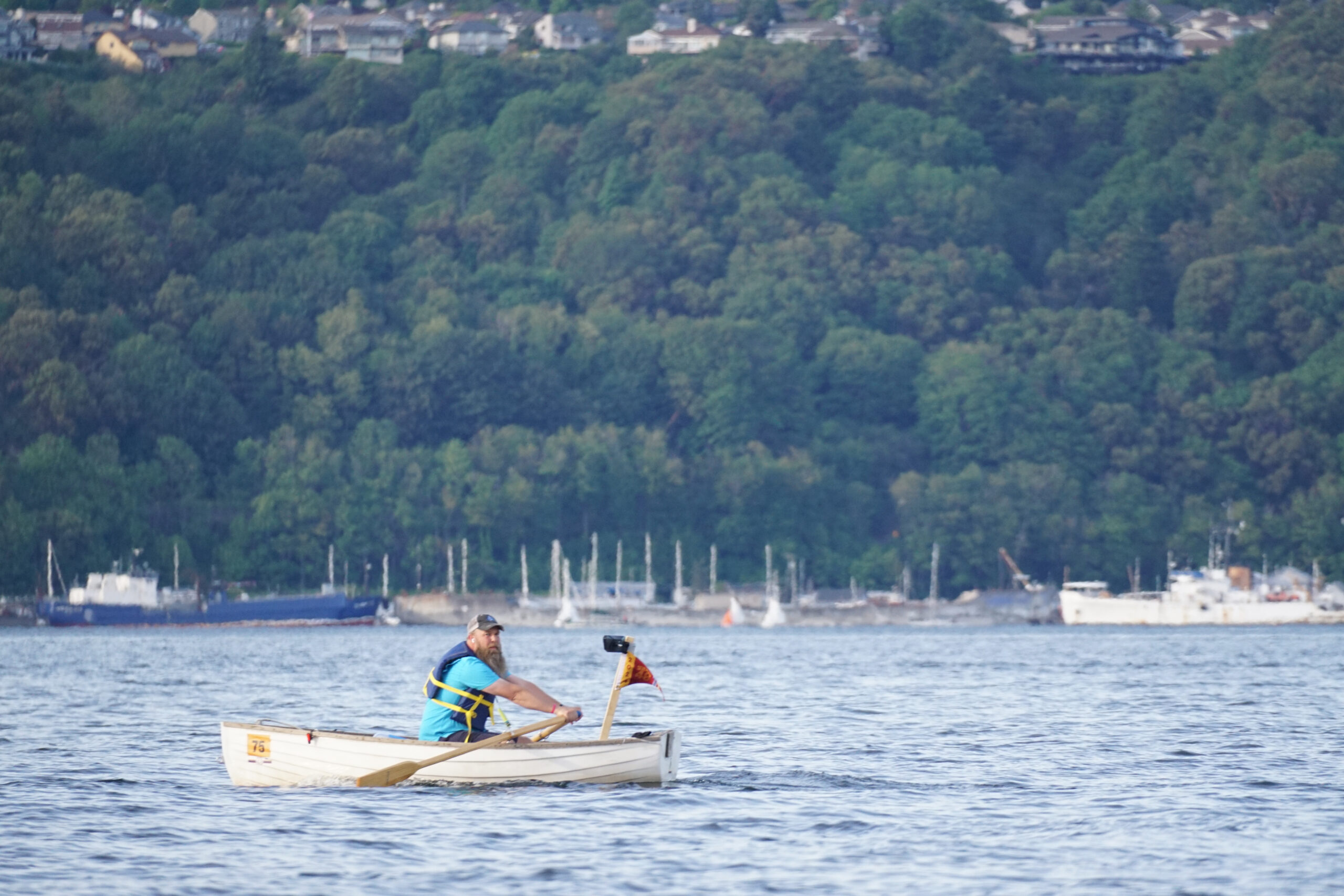It has been a while since I posted a photo of my desk setup. Did a complete change since last time and made the switch to an ultrawide. This is a 49″ monster. I like it a lot more than I expected.
My father, the Dahlia Superstar
My father was interviewed by King 5 News on Aug 17, 2023 in a segment titled, “This Chehalis man is the most humble “superstar” you’ll ever meet”
2024 Family Sailing Trip
Our big family sailing trip for 2024 is in the books! We were out July 3-13. This trip focused on making good memories for the kids. We did short hops, keeping destinations to places with kid friendly activities. So they could get off the boat and have fun. Our route was:– Quartermaster Harbor (4th of
Seventy48 Race Recap – 2024
I was looking north up Colvos Passage, straining against the oars of my 9-foot Minto rowing dinghy. As the sun set, hundreds of lights began to twinkle, marking the other rowboats like little shining stars. Despite the beauty, I felt only disappointment. A few hours earlier, the Seventy48 human-powered boat race had begun. No motors,
At last… Shadow has a windlass and anchor!
It only was three years from the start to finish, but Shadow finally has an anchor installed on her windlass! I may do a full write up on the setup, probably not. Shadow did not come with an anchor setup, so all this is brand new to her. No more hauling up a heavy anchor