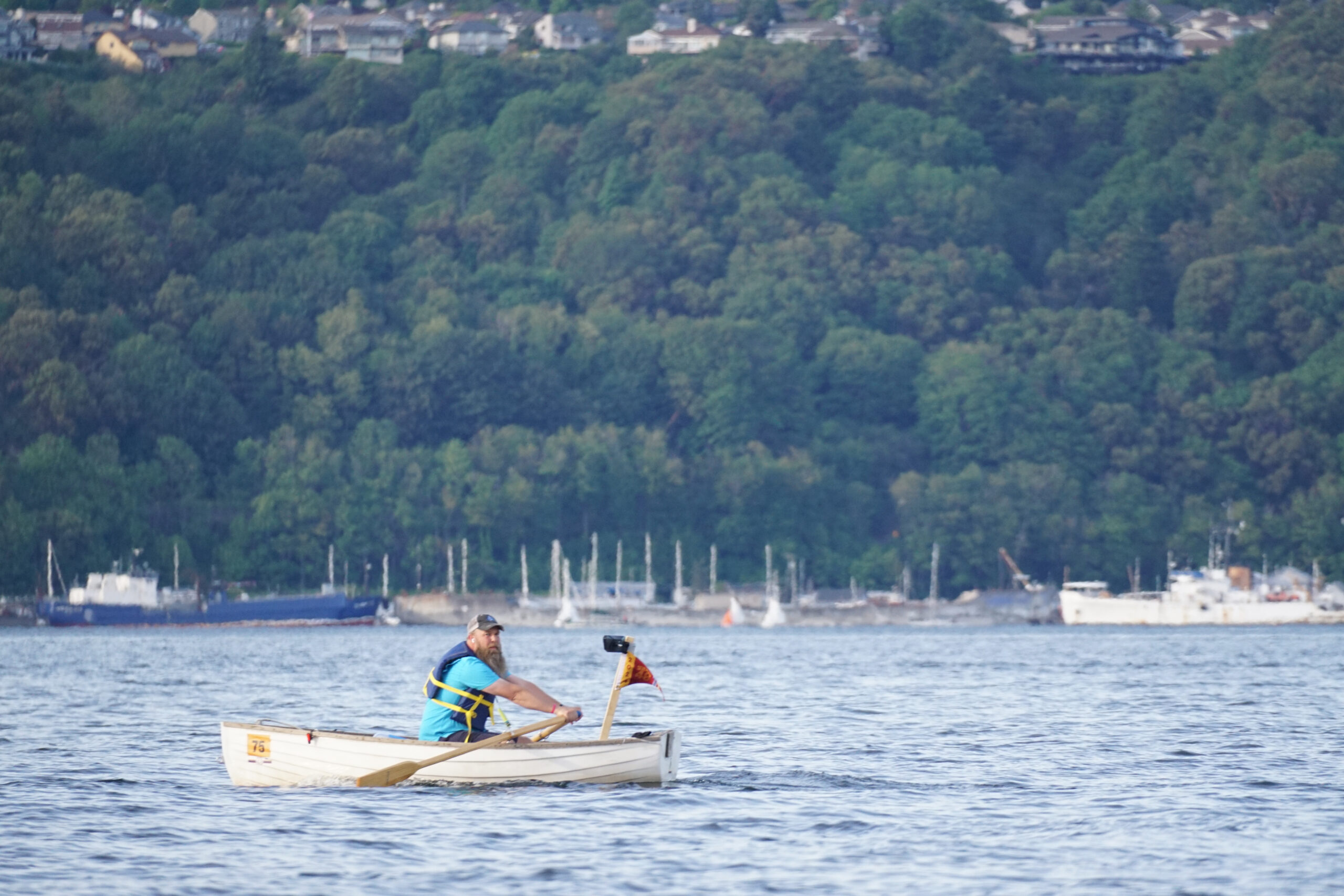Our big family sailing trip for 2024 is in the books! We were out July 3-13. This trip focused on making good memories for the kids. We did short hops, keeping destinations to places with kid friendly activities. So they could get off the boat and have fun. Our route was:– Quartermaster Harbor (4th of
Seventy48 Race Recap – 2024
I was looking north up Colvos Passage, straining against the oars of my 9-foot Minto rowing dinghy. As the sun set, hundreds of lights began to twinkle, marking the other rowboats like little shining stars. Despite the beauty, I felt only disappointment. A few hours earlier, the Seventy48 human-powered boat race had begun. No motors,
At last… Shadow has a windlass and anchor!
It only was three years from the start to finish, but Shadow finally has an anchor installed on her windlass! I may do a full write up on the setup, probably not. Shadow did not come with an anchor setup, so all this is brand new to her. No more hauling up a heavy anchor
Patience diffuses the negative; Kindness initiates the positive
I saw a father in a park the other day. His son was clearly upset about something and acting out. The father squatted down next to him and was patiently trying to sooth him. Soon, the two walked out of the park, hand-in-hand, the son skipping lightly at his side. Meanwhile, several blocks away, another
Compassion
Compassion means listening to someone’s struggles instead of discounting their discomfort. Taking the time to wipe away a tear. Covering their shame instead of exposing it. Sharing the load instead of ignoring it. Photo by Matt Collamer on Unsplash